✨ This blog originally appeared here: View original blog
Sandbox or Production? SaaS or OnPrem? This tiny module gives you the answers before you make a move.
Back when I was a core developer for one of the prominent ISV solutions in Australia, I often found myself juggling multiple Azure instances, one for production, another for UAT, and several dev sandboxes.
It wasn’t just about clean separation; it was about control. Certain Azure Functions or services needed to behave differently depending on the environment. A dev-only trigger running in production? That’s a recipe for disaster.
That’s why environment awareness became non-negotiable. Knowing whether you’re in a sandbox, production, or on-prem instance, before executing logic, can save hours of debugging and prevent costly mistakes.
Today, I’m sharing a simple but powerful way to build that awareness directly into your Business Central extensions using native AL codeunits.
Let’s explore how to surface tenant and environment metadata using AL, before your logic goes live.
Introduction: Why Environment Awareness Matters
In modern Business Central development, especially when integrating with external services like Azure Functions or APIs, context is everything. Whether you're deploying to SaaS, on-prem, or a hybrid setup, your extension needs to know where it’s running.
Hardcoding behavior or relying on manual toggles is risky. Instead, we can leverage built-in AL codeunits to programmatically detect the environment and tenant context. This allows you to:
- Prevent dev/test logic from executing in production
- Tailor UX or diagnostics based on deployment type
- Log or trace behavior differently depending on the environment
- Safeguard sensitive operations with conditional logic
The Tools: Codeunit 433 and Codeunit 457
Codeunit 433 – Azure AD Tenant
This codeunit provides access to the Azure AD tenant ID, which is useful for identifying the customer or instance context.
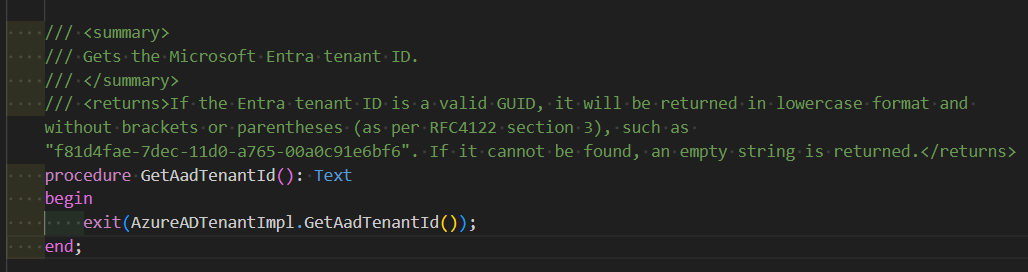
Codeunit 457 – Environment Information
This one’s the real MVP for environment awareness. It exposes methods to check whether you're running in SaaS, on-prem, or a sandbox.
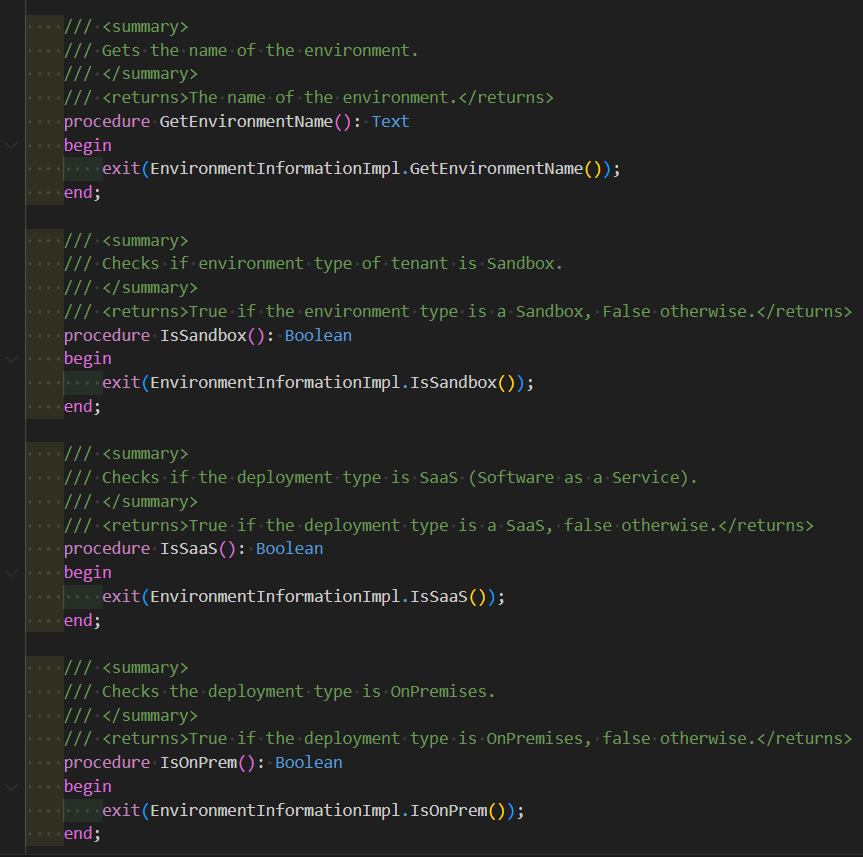
These methods let you write conditional logic like:
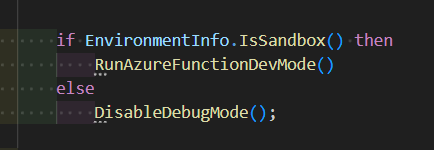
Practical Use Cases
- Azure Function Triggers: Only allow certain functions to run in dev/UAT.
- Telemetry & Logging: Add verbose logs in sandbox, suppress in production.
- Feature Flags: Enable experimental features only in safe environments.
- Client-Specific Logic: Tailor behavior based on tenant ID for internal testing.
Best Practices
- Centralize environment checks in a helper codeunit to avoid duplication and improve maintainability.
- Never hardcode logic without safeguards, always validate the environment before executing sensitive operations.
- Use tenant ID checks sparingly and only when you control or trust the tenant context (e.g., internal dev/test tenants).
- Combine IsSandbox() and tenant ID checks for layered control in multi-tenant setups.
- Log environment context during startup or diagnostics to improve traceability and support.
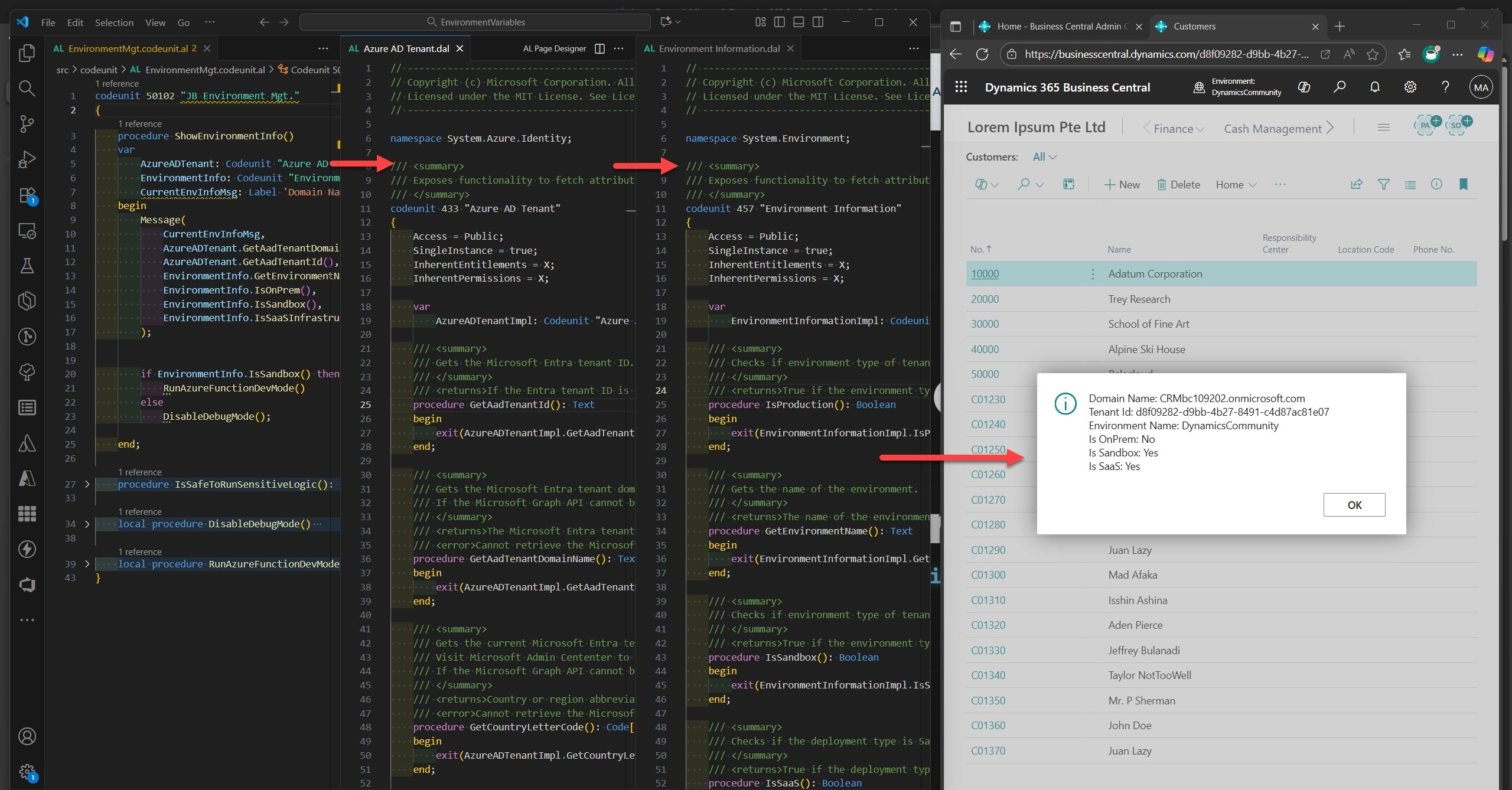
✨ Demo in Action:
📌 Key Takeaways
- You can programmatically detect environment type using Environment Information (Codeunit 457).
- You can retrieve the Azure AD tenant ID using Azure AD Tenant (Codeunit 433).
- These checks help prevent dev/test logic from leaking into production.
- Wrapping logic in a reusable helper module improves clarity and safety.
💡 Gotchas to Watch For
- Tenant ID isn’t foolproof, it can change if the client migrates or restructures their Azure setup.
- Sandbox doesn’t always mean safe, some clients use sandbox environments for semi-live testing.
- OnPrem detection may vary depending on hybrid deployments or custom hosting setups.
- Environment checks don’t replace proper CI/CD discipline, use them as guardrails, not crutches.
⌛ Closing Thoughts
Environment awareness is one of those quiet heroes in extension development. It doesn’t shout, but it saves you from shouting later. Whether you're building internal tools, client-facing features, or integrating with external services, knowing your context is key.
By using native AL codeunits like 433 and 457, you’re not just writing reactive code, you’re designing proactive solutions. And in a world of multi-tenant SaaS, that’s the kind of foresight that sets great developers and consultants apart.
📣 Stay Tuned
Stay tuned as we continue modularizing AL patterns, echoing real-world consulting work, and delivering practical solutions for Business Central, one Saturday at a time.
This week’s drop highlights how environment awareness can safeguard your extensions and empower smarter logic across tenants and deployments.
♻️ Repost to support the community and follow Jeffrey Bulanadi for clear, technical insights above and beyond Business Central and AL development.
🔗 Demo Repository: Explore my GitHub sample showcasing environment-aware logic in AL: EnvironmentAwarenessDemo on GitHub
Helpful Reference:
Codeunit "Environment Information" – Microsoft Learn
Codeunit "Azure AD Tenant" – Microsoft Learn
#BCSaturdayCodeHacks #Dynamics365 #MSDyn365 #MSDyn365BC #BusinessCentral #ALDevelopment #DevTips #EnvironmentAwareness #AzureAD #ConsultingLife

Join the Conversation
Share your thoughts, ask questions, or discuss this article with the community. All comments are moderated to ensure quality discussions.
No comments yet
Be the first to start the conversation!
0 Comments
Leave a Comment